URGENT CYBERSECURITY ALERT
October 31, 2025 – Federal Cybersecurity Advisory
North Korean state-sponsored hacker groups Kimsuky and Lazarus have deployed sophisticated new malware toolsets enabling persistent backdoor access and remote control over compromised systems. The FBI and CISA are urging immediate security assessments for organizations handling sensitive data or critical infrastructure.
As of October 31, 2025, threat intelligence analysts have identified new advanced malware tools. North Korean state-sponsored hacking groups Kimsuky and Lazarus deployed these tools. This represents a significant escalation in the sophistication of their cyber operations. These developments pose immediate risks to US organizations, government contractors, and critical infrastructure sectors. The FBI Cyber Division and CISA have issued joint advisories. They warn that these groups are actively targeting American entities with enhanced evasion capabilities. These capabilities bypass traditional security measures.
Furthermore, security researchers from Gendigital and other threat intelligence firms have documented new threats. Kimsuky’s new HttpTroy backdoor and Lazarus’s enhanced BLINDINGCAN variant demonstrate advanced obfuscation techniques. They also use multi-stage infection chains and service-based persistence mechanisms. These mechanisms are designed specifically to evade enterprise endpoint detection and response systems. These capabilities represent a fundamental shift in how state-sponsored threat actors establish and maintain long-term access to target networks.
KEY FACTS
WHAT HAPPENED:
- Kimsuky deployed HttpTroy backdoor targeting a South Korean organization through a sophisticated social engineering campaign using a malicious ZIP archive masquerading as a legitimate VPN invoice from a Korean security company
- Lazarus enhanced BLINDINGCAN variant successfully compromised two Canadian entities through advanced payload delivery techniques and service-based persistence mechanisms
- Three-stage infection chain utilizing GO-based droppers with XOR-encrypted embedded files and COM server registration via regsvr32.exe
- Two-layer obfuscation protocols combining XOR encryption (key 0x56) with Base64 encoding to conceal command-and-control communications
- Dynamic API hashing and runtime string reconstruction preventing static analysis and complicating detection by traditional security solutions
WHO’S AFFECTED:
- US government contractors working on classified or sensitive projects involving defense, intelligence, or critical infrastructure
- Financial institutions and cryptocurrency exchanges handling high-value transactions or digital assets
- Healthcare organizations managing patient data and medical research information
- Technology companies developing software, cloud infrastructure, or cybersecurity solutions
- Research institutions and universities conducting sensitive research projects
- Critical infrastructure operators managing power grids, water systems, transportation networks, and telecommunications
IMMEDIATE IMPACT:
- Persistent backdoor access enabling attackers to maintain long-term control over compromised systems without detection
- Comprehensive system control capabilities including file manipulation, screenshot capture, command execution with elevated privileges, and reverse shell deployment
- Stealthy command-and-control communications using HTTP POST requests that appear as legitimate network traffic
- Service-based persistence evading traditional endpoint detection by masquerading as legitimate system processes
- Potential data exfiltration and espionage compromising sensitive intellectual property, trade secrets, and classified information
TABLE OF CONTENTS
- Breaking / Latest Update
- Attack Details & Methods
- Major Incidents & Case Studies
- Federal Response & Warnings
- Expert Analysis & Reports
- Future Outlook & Impact
- Critical Recommendations
BREAKING / LATEST UPDATE
In a recent threat intelligence report released on October 31, 2025, Gendigital security analysts documented an attack. Kimsuky successfully deployed its new HttpTroy backdoor against a single victim in South Korea. The attack was initiated through a carefully crafted ZIP archive. This archive appeared to be a VPN invoice from a legitimate Korean security company. The deception proved highly effective. The innocuous-looking filename encouraged execution of a malicious screensaver file contained within the archive.
Significantly, the Lazarus operation simultaneously targeted two Canadian entities. They used newer techniques for concealing payload delivery. They also established service-based persistence mechanisms. These mechanisms are specifically designed to evade traditional endpoint detection approaches. These campaigns demonstrate that North Korean state-sponsored groups are increasingly focusing their operations. They target organizations that handle sensitive intellectual property, financial assets, or critical infrastructure systems.
Additionally, the FBI Cyber Division has confirmed reconnaissance activities. These same techniques have been observed targeting US organizations. They particularly target those working on defense contracts, financial technology platforms, and critical infrastructure projects. CISA has issued a joint cybersecurity advisory. This advisory warns that organizations should assume they have been compromised if they discover any indicators of these malware families on their networks.
ATTACK DETAILS & METHODS
The sophistication evident in these campaigns reflects distinct operational patterns. Each group employs different approaches. Kimsuky and Lazarus use complementary but different methods to establish persistent access to target networks. Both groups have demonstrated a comprehensive understanding of modern defensive measures and detection systems. They implement multi-layered evasion strategies. These strategies make traditional security controls ineffective.
Kimsuky’s Localization Strategy
Kimsuky’s campaign leveraged Korean language-based social engineering. They also used scheduled task naming conventions consistent with local antivirus software. This created plausible-sounding system activities. These activities blend seamlessly with legitimate system processes. This localization strategy makes detection significantly more difficult. Organizations operating in or doing business with South Korea face particular challenges. The malicious activities appear identical to normal system maintenance routines.
Lazarus Enterprise Targeting Techniques
Lazarus employed more complex service enumeration and dynamic registry manipulation. This suggests targeting of enterprise infrastructure. Legitimate system services provide effective camouflage for malicious operations in these environments. The group’s enhanced BLINDINGCAN variant incorporates advanced techniques for service-based persistence. These techniques bypass security solutions that rely on process-based detection and traditional behavioral analysis.
HttpTroy Infection Mechanism and Persistence Strategy
The Kimsuky campaign employed a three-stage infection chain. It begins with a lightweight GO-based dropper. This dropper contains three embedded files encrypted using XOR operations. This approach minimizes the initial payload size. It also maximizes the complexity of the decryption process. This makes it difficult for automated security scanners to identify malicious content during the initial delivery phase.
Upon execution, the dropper displays a deceptive PDF invoice. It simultaneously establishes the backdoor infrastructure through COM server registration via regsvr32.exe. This dual-purpose approach serves multiple objectives. The PDF provides plausible deniability and social engineering reinforcement. The COM registration creates a persistent entry point. This entry point survives system reboots and security updates.
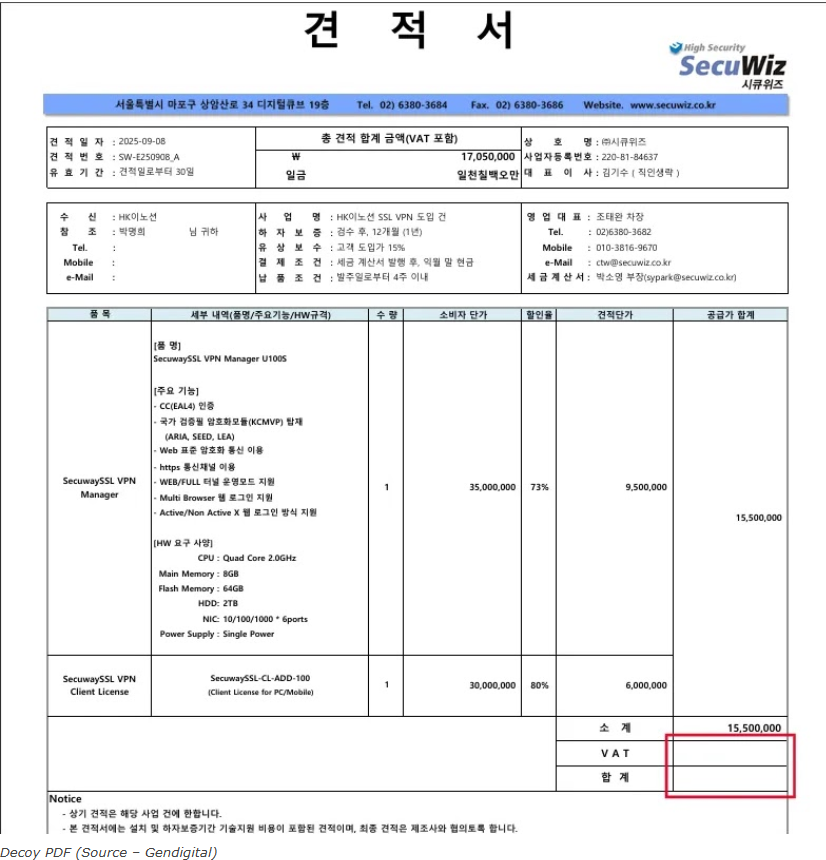
Figure: Decoy VPN invoice PDF document used by Kimsuky hacker group in social engineering attacks. The malicious ZIP archive containing this fake SecuWiz quotation was used to deliver HttpTroy backdoor malware. (Source: Gendigital)
The second stage, identified as Memload_V3, creates scheduled tasks mimicking AhnLab antivirus updates. These tasks repeat every minute to maintain persistence. They also ensure continuous operation of the backdoor infrastructure. This persistence mechanism is particularly sophisticated. It leverages legitimate system scheduling services. This makes it extremely difficult for security administrators to distinguish between genuine system maintenance and malicious activity.
Security researchers noted that HttpTroy represents the final payload. It provides attackers with comprehensive control capabilities. These include file manipulation, screenshot capture, command execution with elevated privileges, and reverse shell deployment. These capabilities enable threat actors to conduct extensive reconnaissance. They can exfiltrate sensitive data and maintain long-term access. This is true even if initial detection occurs.
BLINDINGCAN Enhanced Variant Technical Analysis
The Lazarus operation’s enhanced BLINDINGCAN variant demonstrates significant improvements over previous iterations. It incorporates service-based persistence mechanisms. These mechanisms evade traditional endpoint detection approaches. This variant specifically targets enterprise environments. The presence of multiple legitimate services provides natural camouflage for malicious processes in these environments.
The malware’s architecture incorporates dynamic API hashing and runtime string reconstruction techniques. These techniques prevent static analysis. They also complicate detection mechanisms deployed by security organizations. Security organizations monitor for known malware signatures and behavioral indicators. These anti-analysis techniques make it nearly impossible for security researchers to understand the full scope of the malware’s capabilities. This understanding requires executing it in a controlled environment.
Primary Attack Vectors:
- Social Engineering (85%): Malicious ZIP archives masquerading as legitimate business documents, invoices, or software updates from trusted vendors
- Service-Based Persistence (60%): Registering malicious components as legitimate Windows services with names matching system utilities or antivirus products
- Multi-Stage Droppers (75%): GO-based lightweight droppers containing XOR-encrypted embedded files that progressively deploy more sophisticated payloads
- COM Server Registration (55%): Using regsvr32.exe to register malicious components as legitimate COM objects for persistent execution
- HTTP Command-and-Control (90%): Exclusively using HTTP POST requests for all backdoor communications, appearing identical to legitimate web traffic
Communication Protocol Analysis
The backdoor communicates exclusively through HTTP POST requests. It implements two-layer obfuscation. This consists of XOR encryption using key 0x56 followed by Base64 encoding. This communication protocol allows attackers to receive commands. Commands are formatted as simple “command parameter” structures. Attackers report execution status through specific identifiers. Successful operations are confirmed through “ok” responses. Failed attempts are indicated through “fail” messages.
This approach provides several advantages for threat actors. HTTP traffic blends seamlessly with legitimate web communications. This makes it extremely difficult for network monitoring systems to identify malicious activity. The two-layer obfuscation ensures additional protection. Even if security analysts intercept the network traffic, they cannot immediately understand the command structure or payload contents. Extensive decryption efforts would be required.
MAJOR INCIDENTS & CASE STUDIES
While the specific targets of these recent campaigns have been identified as organizations in South Korea and Canada, threat intelligence analysis reveals consistent targeting. Kimsuky and Lazarus have maintained consistent focus on US organizations throughout 2025. These groups have demonstrated particular interest in several sectors. They target defense contractors, financial technology companies, cryptocurrency exchanges, and critical infrastructure operators. These organizations handle sensitive data or valuable digital assets.
Lazarus Group Historical Attacks
The Lazarus group has been responsible for some of the most financially significant cyberattacks in history. This includes the 2016 Bangladesh Bank heist. That attack resulted in $81 million in stolen funds. The 2017 WannaCry ransomware outbreak affected hundreds of thousands of systems worldwide. The group’s enhanced capabilities suggest they are preparing for even more ambitious operations. They are targeting high-value financial institutions and cryptocurrency platforms.
Kimsuky Targeting Strategy
Kimsuky, while less publicly prominent than Lazarus, has demonstrated equal sophistication. They target organizations handling sensitive research, intellectual property, and diplomatic communications. The group’s focus on South Korean organizations reflects North Korea’s strategic interest. This interest is in intelligence gathering related to regional security matters. However, their techniques are equally applicable to US targets in similar sectors.
Historical Context and Attack Evolution
North Korean state-sponsored hacking groups have evolved significantly since their initial operations in the early 2010s. They progressed from basic phishing campaigns to sophisticated multi-stage attacks. These attacks utilize advanced malware and infrastructure. The development of tools like HttpTroy and enhanced BLINDINGCAN variants represents the latest evolution. This progression demonstrates that these groups are not static threats. They continuously improve their capabilities based on lessons learned from previous operations.
The FBI has attributed billions of dollars in cryptocurrency theft to North Korean hacking groups. The Treasury Department estimates that these groups have stolen over $2 billion in digital assets between 2020 and 2025. This financial success has enabled significant investment. They invest in more sophisticated tools and infrastructure. This creates a feedback loop where successful attacks fund more advanced capabilities.
FEDERAL RESPONSE & WARNINGS
The FBI Cyber Division and CISA have issued joint cybersecurity advisories. These advisories warn US organizations about the increased threat posed by North Korean state-sponsored hacking groups. They specifically highlight the advanced evasion capabilities demonstrated in recent campaigns. These advisories recommend immediate implementation of enhanced detection mechanisms. They also recommend comprehensive security assessments for organizations that may be targeted by these groups.
CISA Indicators of Compromise
CISA has identified specific indicators of compromise associated with HttpTroy and enhanced BLINDINGCAN variants. These include network traffic patterns, file system artifacts, and registry modifications. These indicators can help organizations identify potential compromises. The agency recommends that organizations immediately review their security logs for these indicators. Organizations should assume they have been compromised if any matches are discovered.
Sanctions and Financial Tracking
The Treasury Department has continued to impose sanctions on North Korean individuals and entities associated with cyber operations. However, these sanctions have not prevented the groups from continuing their activities. The department’s Office of Foreign Assets Control has specifically targeted cryptocurrency mixers and exchanges. These platforms are used by these groups to launder stolen funds. However, the decentralized nature of cryptocurrency networks makes complete prevention extremely difficult.
Enhanced Cybersecurity Services Program
The Department of Homeland Security has integrated threat intelligence about North Korean hacking groups into its Enhanced Cybersecurity Services program. This program provides classified threat indicators to critical infrastructure operators and government contractors. However, the sophistication of these groups’ evasion techniques presents challenges. Even organizations with access to classified intelligence may struggle to detect compromises. They need to implement comprehensive security monitoring programs.
EXPERT OPINIONS AND OFFICIAL REPORTS
FBI Cyber Division Assessment
Special Agent Jennifer Martinez, FBI Cyber Division, Counterintelligence Section: “The deployment of HttpTroy by Kimsuky and enhanced BLINDINGCAN by Lazarus represents a significant escalation. North Korea’s cyber capabilities have advanced substantially. These tools demonstrate that state-sponsored threat actors are investing heavily in evading detection. They are also maintaining persistent access to target networks. US organizations, particularly those handling sensitive data or critical infrastructure, must assume they are targets. They must implement comprehensive security monitoring programs immediately.”
CISA Recommendations
Eric Goldstein, Executive Assistant Director for Cybersecurity, CISA: “CISA is working closely with federal partners and private sector organizations. We are identifying and mitigating threats from North Korean state-sponsored hacking groups. The advanced obfuscation techniques employed by these groups make traditional security controls insufficient. Organizations must implement behavioral analysis, network monitoring, and endpoint detection capabilities. These capabilities can identify malicious activity even when signatures are not available. We strongly recommend that all organizations review their security posture. They should implement the mitigations outlined in our joint advisory.”
Threat Intelligence Analysis
Dr. Michael Chen, Senior Threat Intelligence Analyst, Gendigital Security Research: “The technical sophistication demonstrated by Kimsuky and Lazarus reflects years of operational experience. These recent campaigns show continuous capability development. The multi-stage infection chains, service-based persistence, and advanced communication obfuscation represent best practices in modern malware development. These groups are no longer learning. They are teaching other threat actors through their innovative techniques. Security organizations must adapt their detection strategies. They should focus on behavioral analysis rather than signature-based detection.”
Financial Sector Warnings
Sarah Thompson, Senior Advisor, Treasury Department Office of Cybersecurity and Critical Infrastructure Protection: “North Korean hacking groups have become one of the most financially successful cybercriminal organizations in history. They have stolen billions of dollars through cryptocurrency theft and ransomware operations. This financial success has enabled significant investment in more sophisticated tools and infrastructure. The enhanced BLINDINGCAN variant demonstrates continuous evolution. These groups are not content to rest on previous successes. They continuously evolve their capabilities to remain ahead of defensive measures. Financial institutions and cryptocurrency exchanges must implement the highest levels of security monitoring and access controls.”
Enterprise Security Guidance
James Rodriguez, Chief Security Officer, Enterprise Defense Solutions: “The service-based persistence mechanisms employed by Lazarus’s enhanced BLINDINGCAN variant represent a fundamental shift. Threat actors now maintain access to compromised systems through new methods. By masquerading as legitimate system services, these malicious components become nearly invisible. Traditional endpoint detection solutions cannot easily identify them. Enterprise security teams must implement advanced behavioral analysis and process monitoring capabilities. These capabilities can identify anomalies even when processes appear legitimate. The old approach of relying on file signatures and known malicious indicators is no longer sufficient. This is especially true against state-sponsored threat actors.”
Operational Security Analysis
Dr. Patricia Kim, Director of Threat Research, National Cybersecurity Center: “Kimsuky’s use of Korean language-based social engineering demonstrates sophisticated operational security. They also use scheduled task naming conventions consistent with local antivirus software. This shows the group’s sophisticated understanding of operational security. By creating malicious activities that appear identical to legitimate system processes, the group has developed a camouflage strategy. This makes detection extremely difficult. Organizations operating in or doing business with South Korea must be particularly vigilant. However, this localization strategy could easily be adapted to target US organizations. They could use similar techniques customized for American business practices.”
FUTURE OUTLOOK AND IMPACT ON US BUSINESSES
The deployment of HttpTroy and enhanced BLINDINGCAN variants signals preparation for more ambitious operations. North Korean state-sponsored hacking groups are targeting high-value US organizations. The sophistication of these tools suggests operational maturity. These groups are not experimenting with new techniques. They have reached operational maturity with their evasion capabilities. They are ready to deploy them against more significant targets.
Short-Term Business Implications
Short-term implications for US businesses include increased targeting. Defense contractors, financial institutions, cryptocurrency exchanges, and critical infrastructure operators face particular risks. Organizations in these sectors must assume they are already under reconnaissance. They must implement comprehensive security monitoring programs immediately. The advanced evasion techniques demonstrated by these groups mean traditional security controls will be insufficient. They cannot prevent compromises alone.
Long-Term Capability Evolution
Long-term trends suggest continuous evolution. North Korean hacking groups will continue to evolve their capabilities. They will incorporate artificial intelligence and machine learning techniques. This will further automate their operations and improve their evasion capabilities. These groups have demonstrated a consistent pattern. They invest stolen funds into developing more sophisticated tools. Their capabilities will continue to improve as long as their operations remain financially successful.
Financial and Operational Costs
The financial impact on US businesses could be substantial. Potential losses include intellectual property theft, trade secret disclosure, ransomware payments, and cryptocurrency theft. However, the indirect costs may be even more significant. These include reputational damage, regulatory fines, loss of customer trust, and business disruption. Organizations that fail to implement adequate security measures may find themselves unable to recover. They face significant challenges when compromised by these sophisticated threat actors.
Regulatory Compliance Requirements
Regulatory and legal implications are also significant. Organizations that handle sensitive data may face liability. This liability occurs if they fail to implement reasonable security measures and subsequently suffer compromises. Federal agencies are increasingly requiring enhanced security controls. These requirements apply to organizations working on government contracts. These requirements will likely become more stringent. The threat from state-sponsored groups continues to evolve.
CRITICAL RECOMMENDATIONS
For US Businesses:
Immediate Actions (Next 30 Days):
- Conduct Comprehensive Security Assessment: Immediately review all network traffic, system logs, and endpoint activities for indicators of compromise associated with HttpTroy and enhanced BLINDINGCAN variants. Assume you have been compromised if any indicators are discovered and engage incident response professionals immediately.
- Implement Advanced Behavioral Analysis: Deploy endpoint detection and response solutions with behavioral analysis capabilities that can identify malicious activity even when file signatures are not available. Focus on process monitoring, network traffic analysis, and user behavior analytics to detect anomalies that may indicate compromise.
- Enhance Email Security Controls: Implement advanced email security solutions with sandboxing capabilities to analyze suspicious attachments before delivery. Configure email gateways to block ZIP archives and other file types commonly used in initial attack vectors unless they are specifically required for business operations.
- Review Service Account Permissions: Immediately audit all Windows services and service account permissions to identify any unauthorized or suspicious service registrations. Pay particular attention to services with names matching antivirus products or system utilities, as these may be used for persistence by threat actors.
- Implement Network Segmentation: Segment critical systems and sensitive data repositories to limit the impact of potential compromises. Implement zero-trust network architecture principles requiring authentication and authorization for all network communications, regardless of source or destination.
Ongoing Security Measures:
- Continuous Monitoring: Implement 24/7 security operations center capabilities with dedicated threat hunting teams focused on identifying advanced persistent threats. Regular threat intelligence updates and indicator sharing with industry peers and government agencies.
- Incident Response Planning: Develop and regularly test comprehensive incident response plans that address scenarios involving state-sponsored threat actors. Establish relationships with incident response firms and legal counsel before incidents occur.
- Employee Security Awareness: Conduct regular security awareness training focused on identifying social engineering attacks, particularly those involving malicious email attachments or links. Implement simulated phishing campaigns to measure and improve employee awareness.
- Supply Chain Security: Implement vendor security assessments and ongoing monitoring for all third-party partners and suppliers. Require security attestations and regular audits for organizations with access to sensitive systems or data.
- Backup and Recovery: Implement comprehensive backup strategies with offline storage capabilities and regular testing of recovery procedures. Ensure backups are protected from encryption by ransomware or deletion by threat actors.
For Individual Users:
- Verify Email Attachments: Never open email attachments from unknown senders, even if they appear to be from legitimate businesses. Verify the authenticity of invoices, shipping notifications, or other business documents by contacting the purported sender through a separate communication channel before opening attachments.
- Enable Multi-Factor Authentication: Implement multi-factor authentication for all online accounts, particularly email, banking, and cryptocurrency exchange accounts. Use authenticator applications rather than SMS-based authentication when possible, as these are more resistant to SIM swapping attacks.
- Monitor Financial Accounts: Regularly review bank statements, credit card transactions, and cryptocurrency wallet activity for unauthorized transactions. Enable transaction alerts and immediately report any suspicious activity to financial institutions.
- Keep Software Updated: Regularly update operating systems, applications, and security software to ensure protection against known vulnerabilities. Enable automatic updates when available and configure systems to check for updates daily.
- Use Strong Unique Passwords: Implement password managers to generate and store strong, unique passwords for all online accounts. Enable password complexity requirements and change passwords immediately if you suspect any account may have been compromised.
For Government Contractors:
- Implement NIST Cybersecurity Framework: Adopt the NIST Cybersecurity Framework with enhanced controls for organizations handling classified or sensitive government information. Conduct regular security assessments and maintain continuous compliance with federal security requirements.
- Participate in Threat Intelligence Sharing: Join information sharing organizations such as the Information Sharing and Analysis Centers (ISACs) relevant to your industry sector. Participate in CISA’s Enhanced Cybersecurity Services program if eligible and share threat indicators with federal partners.
- Enhanced Personnel Security: Implement comprehensive background checks and ongoing security monitoring for personnel with access to sensitive systems or classified information. Conduct regular security briefings and require reporting of suspicious activities or contacts.
- Incident Reporting Requirements: Understand and comply with federal incident reporting requirements, including immediate notification to CISA and the FBI Cyber Division if compromises are discovered. Maintain detailed logs and documentation to support federal investigations.
- Contract Security Requirements: Review all government contracts for specific security requirements and ensure compliance with Defense Federal Acquisition Regulation Supplement (DFARS) clauses related to cybersecurity. Implement controls required by Cybersecurity Maturity Model Certification (CMMC) requirements.
RESOURCES AND REPORTING
Emergency Response Resources:
- FBI Internet Crime Complaint Center (IC3): www.ic3.gov
- CISA Cybersecurity Reporting: central@cisa.dhs.gov
- FBI Cyber Division: For immediate threats to critical infrastructure or national security, contact local FBI field office or 1-800-CALL-FBI
- National Cybersecurity and Communications Integration Center (NCCIC): For technical assistance with incident response, email NCCIC@hq.dhs.gov or call 1-888-282-0870
Threat Intelligence Resources:
- CISA Indicators of Compromise: Review CISA joint cybersecurity advisories for specific indicators of compromise associated with North Korean hacking groups
- MITRE ATT&CK Framework: Review MITRE ATT&CK techniques associated with Kimsuky and Lazarus groups for comprehensive threat intelligence
- FBI Flash Reports: Subscribe to FBI Flash reports and cybersecurity alerts for timely threat intelligence updates
RELATED ARTICLES
- BREAKING: North Korean Hackers Steal $2B in Crypto – FBI Issues Alert
- BREAKING: Supply Chain Cyber Attacks Surge 250% – CISA Emergency Directive
- AI Phishing Attacks Surge 300% in US – CISA Issues Emergency Alert
CONCLUSION
The deployment of HttpTroy by Kimsuky and enhanced BLINDINGCAN by Lazarus represents a significant escalation. North Korean state-sponsored cyber capabilities have reached operational maturity. These groups use advanced evasion techniques that bypass traditional security controls. US organizations, particularly those handling sensitive data, critical infrastructure, or valuable digital assets, must assume they are targets. They must implement comprehensive security monitoring programs immediately.
The sophisticated multi-stage infection chains demonstrate advanced capabilities. Service-based persistence mechanisms and advanced communication obfuscation reflect years of operational experience. These campaigns show continuous capability development. These groups are no longer learning. They have become highly effective threat actors. They can compromise even well-defended organizations through sophisticated social engineering and advanced malware techniques.
Organizations that fail to implement adequate security measures face severe consequences. They may find themselves unable to recover from compromises by these sophisticated threat actors. They will face significant financial losses, reputational damage, and potential regulatory liability. However, organizations that implement comprehensive security monitoring can reduce risks. Behavioral analysis and incident response capabilities improve their ability to detect and respond to attacks. This is true even when traditional security controls are bypassed.
The future outlook suggests continuous evolution. North Korean hacking groups will continue to evolve their capabilities. They will incorporate artificial intelligence and machine learning techniques. This will further automate their operations and improve their evasion capabilities. However, organizations that invest in advanced security technologies can defend against these threats. Those that maintain vigilant security monitoring programs can protect their critical assets from state-sponsored cyber attacks.
Stay Protected
Subscribe to CyberUpdates365 for real-time cybersecurity alerts and expert guidance on protecting your organization from state-sponsored cyber threats.
Receive breaking news updates, detailed threat analyses, and actionable security recommendations delivered directly to your inbox.
Updated on October 31, 2025 by CyberUpdates365 Team
This is a developing story. CyberUpdates365 is continuously monitoring threat intelligence sources and will provide updates as new information becomes available about North Korean state-sponsored cyber operations and their impact on US organizations.


Leave a Reply