Sophisticated banking trojan uses advanced evasion techniques to mimic human typing patterns and bypass behavioral biometrics security systems
October 29, 2025 – Global
New Android banking trojan Herodotus targets users in Italy and Brazil
Malware mimics human behavior to bypass biometric detection systems
Advanced evasion techniques pose significant threat to mobile banking security
KEY FACTS
- Malware Name: Herodotus Android banking trojan
- Primary Capability: Mimics human typing behavior to bypass biometric detection
- Target Regions: Italy and Brazil (active campaigns confirmed)
- Distribution Method: Malware-as-a-Service (MaaS) offered by threat actor K1R0
- Infection Vector: Side-loading through SMiShing campaigns
- Detection Bypass: Randomizes character input delays (300-3000ms) to mimic human typing
MALWARE ANALYSIS & TECHNICAL DETAILS
Threat Discovery and Classification
As of October 29, 2025, cybersecurity researchers have identified a sophisticated Android banking trojan named Herodotus that introduces groundbreaking techniques to evade detection systems. During routine monitoring of malicious distribution channels, the malware appeared alongside notorious variants like Hook and Octo.
However, despite sharing distribution infrastructure with other malware families, Herodotus represents a distinct threat that combines elements from the Brokewell malware family with original code specifically designed for advanced evasion and behavioral mimicry.
Human Behavior Mimicry Technology
What sets Herodotus apart from traditional banking trojans is its revolutionary approach to mimicking human behavior during remote control sessions. Specifically, the malware implements sophisticated techniques designed to bypass behavioral biometrics detection systems that are increasingly deployed by financial institutions.
In contrast, traditional remote access trojans typically set text directly in input fields using the ACTION_SET_TEXT function or clipboard manipulation, delivering complete text strings instantaneously. Consequently, this machine-like behavior creates suspicious patterns that behavioral anti-fraud systems easily detect as automated attack indicators.
Advanced Evasion Techniques
Herodotus implements a novel technique where operator-specified text is split into individual characters, with each character set separately at randomized intervals. Additionally, the malware introduces delays ranging from 300 to 3000 milliseconds between character input events, effectively replicating natural human typing patterns.
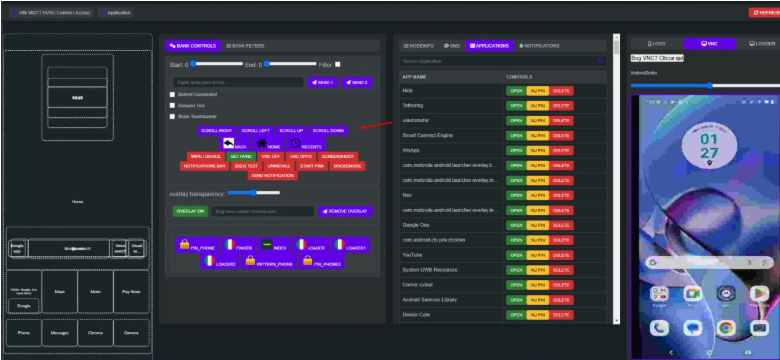
Figure 1: Herodotus malware control panel interface showing advanced device takeover capabilities and human behavior mimicry settings source : Threat Fabric
The malware panel includes a checkbox labeled “Delayed text” that operators can toggle to enable human-like input simulation. While this randomization attempts to evade rudimentary behavioral detection systems that measure input timing, sophisticated systems modeling individual behavior can still identify anomalies.
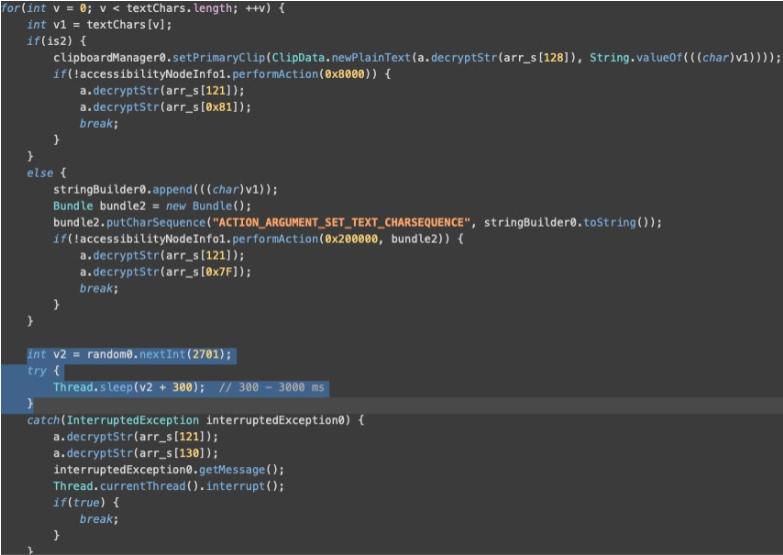
Figure 2: Major capabilities of the Herodotus.A Android Trojan, illustrating its advanced techniques for distribution, credential stealing, DTO fraud, and resilience source: Threat Fabric
INFECTION CHAIN & DEPLOYMENT
Initial Compromise
The malware operates through an infection chain beginning with side-loading, potentially involving SMiShing campaigns that lead victims to malicious download links. Once deployed, Herodotus leverages a custom dropper specifically designed to bypass Android 13+ restrictions on Accessibility Services.
Following installation, the dropper automatically launches the payload and opens Accessibility Service settings, prompting victims to enable the service while displaying a deceptive loading screen overlay that conceals the granting of dangerous permissions.
Data Collection and Targeting
Following successful deployment, Herodotus collects installed application lists and transmits this data to its command-and-control server. Subsequently, the server responds with targeted application lists and corresponding overlay links, enabling the trojan to deploy fake credential-harvesting screens over legitimate banking applications.
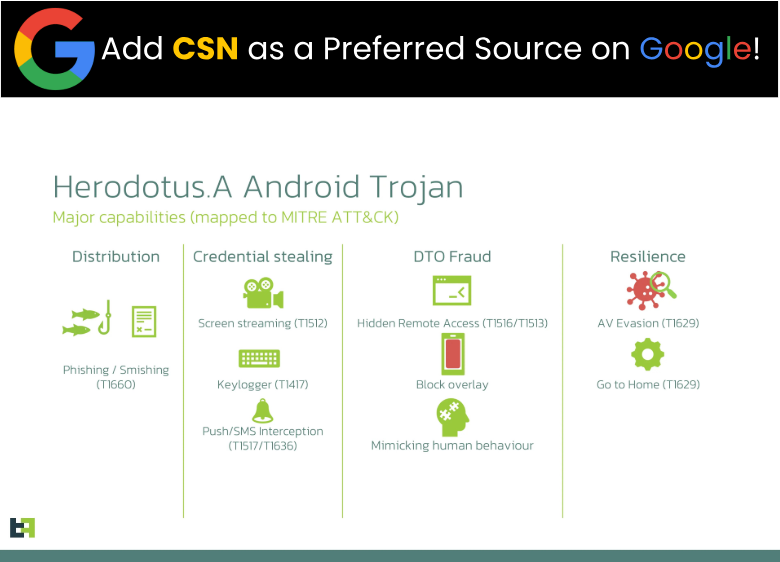
Figure 3: Code snippet demonstrating Herodotus malware’s human behavior mimicry implementation with randomized delays (300-3000ms) and accessibility service abuse source: Threat Fabric
Furthermore, the malware captures login credentials and two-factor authentication codes through SMS interception, providing attackers with complete access to victims’ financial accounts and sensitive information.
FEDERAL RESPONSE & SECURITY WARNINGS
Cybersecurity agencies are monitoring the emergence of Herodotus and similar advanced banking trojans that employ behavioral mimicry techniques. Indeed, the sophistication of these evasion methods represents a significant escalation in mobile banking security threats.
Consequently, financial institutions are being advised to implement multi-layered behavioral biometrics systems that can detect more subtle anomalies in user behavior patterns, as traditional timing-based detection methods may be insufficient against this new generation of malware.
Meanwhile, law enforcement agencies are investigating the underground forums where Herodotus is being offered as Malware-as-a-Service, with particular focus on the threat actor K1R0 and associated distribution networks.
EXPERT OPINIONS
ThreatFabric researchers emphasize that Herodotus follows modern banking trojan trends while introducing capabilities that distinguish it from other device takeover malware. Notably, the ability to mimic human behavior during remote control sessions represents a significant advancement in malware evasion techniques.
Similarly, mobile security experts note that this type of behavioral mimicry poses particular challenges for financial institutions that rely on behavioral biometrics as a primary fraud detection mechanism. As a result, the randomization of input timing makes it increasingly difficult to distinguish between legitimate users and sophisticated attackers.
Additionally, cybersecurity analysts warn that the Malware-as-a-Service model used by Herodotus makes this threat accessible to a broader range of attackers, potentially leading to increased incidents of mobile banking fraud across multiple regions.
FUTURE OUTLOOK
The emergence of Herodotus represents a concerning trend in mobile malware development, where attackers are increasingly focusing on evading behavioral detection systems rather than simply avoiding signature-based detection. Therefore, this shift suggests that financial institutions will need to invest in more sophisticated behavioral analysis technologies.
Looking ahead, security researchers predict that similar behavioral mimicry techniques will likely be adopted by other malware families, creating a new arms race between attackers and defenders in the mobile banking security space.
CRITICAL RECOMMENDATIONS
For Android Users:
- Avoid Side-Loading: Only download apps from official app stores (Google Play Store)
- Enable Google Play Protect: Keep automatic scanning enabled for malware detection
- Review App Permissions: Be cautious of apps requesting Accessibility Services permissions
- Update Regularly: Keep Android OS and security patches up to date
- Monitor Account Activity: Regularly check banking and financial app activity
For Financial Institutions:
- Enhanced Behavioral Analysis: Implement multi-layered behavioral biometrics systems
- Real-Time Monitoring: Deploy advanced fraud detection that analyzes typing patterns
- User Education: Provide customers with guidance on mobile banking security
- Incident Response: Develop protocols for handling behavioral mimicry attacks
- Threat Intelligence: Monitor emerging malware techniques and evasion methods
For Security Professionals:
- Behavioral Modeling: Develop more sophisticated user behavior analysis algorithms
- Threat Hunting: Actively search for malware using behavioral mimicry techniques
- Research Collaboration: Share intelligence about new evasion methods
- Detection Enhancement: Update security tools to identify advanced behavioral patterns
RESOURCES AND REPORTING
Malware Analysis Resources:
- ThreatFabric Research: www.threatfabric.com
- Android Security Guidelines: source.android.com/security
- Google Play Protect: Built into Android devices
Incident Reporting:
- FBI Internet Crime Complaint Center (IC3): www.ic3.gov
- CISA Cybersecurity Reporting: central@cisa.dhs.gov
- Local Law Enforcement: Report mobile banking fraud to local authorities
Detection and Prevention:
- Install reputable mobile security software
- Enable two-factor authentication on all financial accounts
- Monitor bank statements and transaction alerts regularly
- Report suspicious mobile banking activity immediately
RELATED ARTICLES
Stay informed about the latest mobile security threats and malware analysis:
- Samsung Galaxy S25 0-Day Exploited – Hackers Control Camera & Location
- Caminho Malware Uses LSB Steganography to Hide .NET Payloads in Images
- AI Phishing Attacks Surge 300% in US – CISA Issues Emergency Alert
Source: CyberUpdates365
About CyberUpdates365
CyberUpdates365 is your trusted source for real-time cybersecurity intelligence, threat analysis, and security insights. We deliver comprehensive coverage of the latest cyber threats, data breaches, and security vulnerabilities affecting organizations worldwide.
Our expert team provides in-depth analysis, actionable recommendations, and critical security guidance to help businesses and individuals stay protected in an evolving threat landscape. Stay informed with our breaking news alerts, expert insights, and comprehensive security reports.
Subscribe to CyberUpdates365 for real-time cybersecurity alerts and expert guidance on protecting your digital assets.
Cybersecurity Expert | DevOps Engineer
Founder and lead author at CyberUpdates365. Specializing in DevSecOps, cloud security, and threat intelligence. My mission is to make cybersecurity knowledge accessible through practical, easy-to-implement guidance. Strong believer in continuous learning and community-driven security awareness.


Leave a Reply